Computer
and Internet Security Tips
Useful information to help your
computer run smoothly and safely
|
Computer Security Alert
Updated 5-25-2011
by Paul Burns,
Malicious Software Removal Specialist
"The Fake Anti-Virus" Virus! How to Recognize it,
How to Deal With It
|
|
Use of
fake anti-virus, anti-spyware software is a fast-growing
scam, especially as more people become aware of the dangers
of spyware, adware and malware. Fake antivirus programs, or
scareware, are very common and provide a way for scammers to
make easy money. The scammers prey on the fears of Web
surfers who are misled into believing their systems are
infected and then pay, typically, $50 for a program that not
only doesn't protect their computers, but often turns out to
be malicious. The program will typically offer a "Free Virus
Scan" or it may simply report that infections were found and
offer to fix the infections for a fee. The end result is a
loss of money paid, with continued ransom and extortion
tactics and quite often stolen credit card activity or
identity theft. |
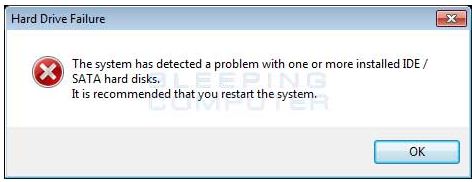
This is an example
of a fake System Alert. Unfortunately, it looks very
much like a legitimate Windows Error Message.
Clicking Yes or No or OK or the standard red "X" in the
upper right corner will activate the
virus. Your best defense is to turn the Computer off
abruptly by holding the computer's power button for 10
seconds or simply pull the power plug.
What ever you
do, Don't click anywhere on the message.
|
| Recently this type of
infection has infiltrated advertising on legitimate
websites. Common infections this month have come from files
planted in Google Search Results. You click on the infected
search result and a small message pops up warning you of a
"Windows System Error" or "Hard Drive Error" |
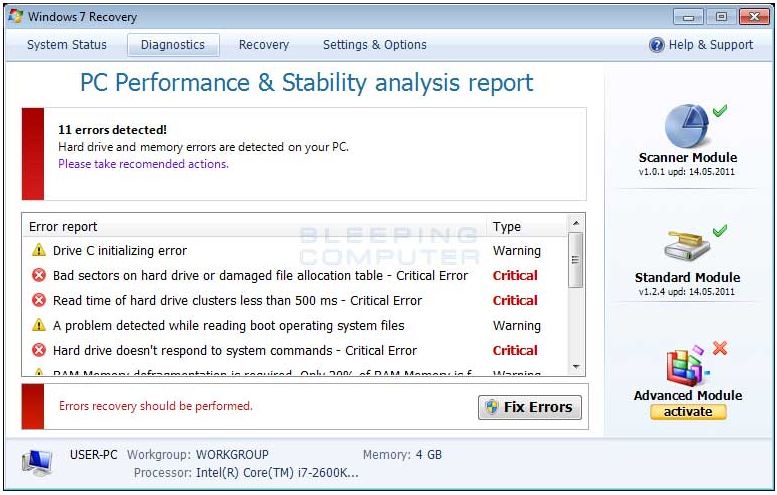
This fake Windows "Repair and
Recovery" Program is an example of what
these programs often look like once activated. |
The window to the left shows a fairly
new infection. Often, by the time this
screen appears the computer is already infected. Once this
window pops up, the computer is completely disabled and held
for ransom until the user agrees to pay.
The
computer's legitimate anti-virus program will have been
disabled, all internet traffic will be re-routed to suit the
virus's needs and all attempts to stop the virus from
working will be intercepted.
The the computer's
normal security software is disabled, removing the virus at
this stage often requires help from somebody who has
experience in malicious software removal. |
| |
You can protect
yourself from becoming infected with this type of malicious
software:
- Keep your Operating System, and
Anti-Virus programs up to date with the programs'
"Automatic Updating" features. Pay attention that your
anti-virus is working properly. When a
virus infects a computer its first goal is to disable the
anti-virus program.
- Know what your normal
anti-virus software's messages looks like. Be suspicious
when a
message looks different than what
you have seen before.
- If you suspect that a
suspicious window has popped up while visiting a website,
just turn the
computer off. Hold the
power button down until the computer shuts off (usually 4 to
5
seconds). This type of virus is often
designed to activate with any mouse click on the window,
even clicking to close the window will activate the virus.
After the computer has stopped, wait
30 seconds
and restart the computer and scan with your normal computer
security software.
- If you recognize that your
computer has become infected, you should seek the help of a
virus removal specialist. At the very least, do any research
on how to remove the infection from a separate computer than
the one that is infected. It is common for a malicious
infection to control or influence the results of search
engines, which could lead to further infection and
ineffective results when searching from the infected
computer.
|